Welcome to Software Development on Codidact!
Will you help us build our independent community of developers helping developers? We're small and trying to grow. We welcome questions about all aspects of software development, from design to code to QA and more. Got questions? Got answers? Got code you'd like someone to review? Please join us.
Post History
Passwords are annoying. Nobody really enjoys passwords, which is why "The End of Passwords" articles keep circulating. I'm looking forward to the day the prediction comes true, but in the meantime ...
#13: Post edited
- Passwords are annoying. Nobody really _enjoys_ passwords, which is why "The End of Passwords" articles keep circulating. I'm looking forward to the day the prediction comes true, but in the meantime passwords are the most common way to do authentication anywhere with a computer.
- I made a chart to classify the important distinctions in making a new password. I'll elaborate on the regions below.
- 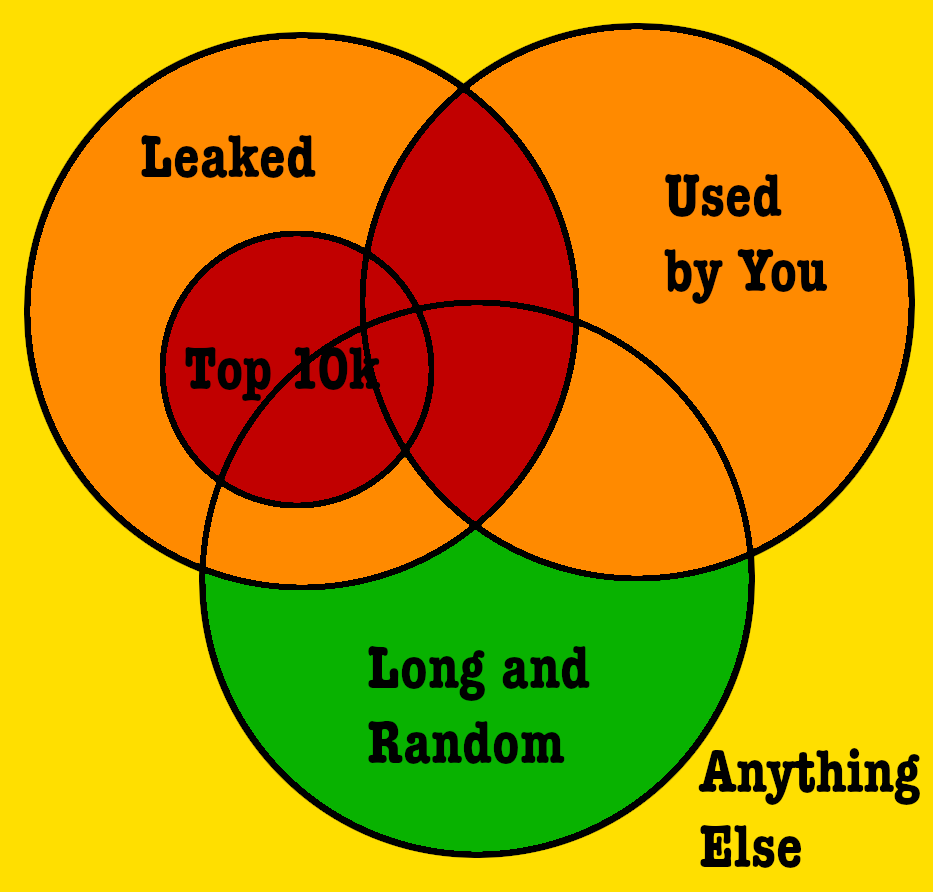
# Bad Passwords## Worst### One of the top-used passwords- Think `abcdef`, `123456`, `iloveyou`, `Pa$$w0rd`, etc. Most of these fall afoul of any website with criteria, but some of them are crafted specifically to get past the "rules."
### A leaked password of _yours_- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And once that combination is public, anyone can do the same.[^hibp]
## Bad### _Any_ leaked password- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
### Any password of _yours_- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
### Stuff about you- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
## Not good### Easy to brute force- Now we're getting to your real question. Like [tarhalda implies][tarhalda], this is the place where attacks typically fall into two modes:
#### Full database exfiltration- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- + The first place they're going to try the password is on the system it came from, but they're going to try it anywhere else you might have an account, too.
#### Vulnerable web service- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts.[^throttling] That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make you change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations[^nist] to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate a [diceware password][diceware] and offer it as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The only nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
# Upshot## Don't- - Don't use anything that can be tied to you.
- - Don't use anything known to be in use by anyone.
- - Don't try to remember all your passwords.
## Do- - Have something to remember the passwords for you.
- - Have something pick completely random passwords[^random] so they are expensive to crack.
## Options- - A password manager from a reputable source[^password-manager]
- - A FIDO key (please have a backup!)
- - A [password card][password-card]
- - A physical notebook
- [^nist]: Between 2003 and 2017, NIST had the 90-day expiration and letters / numbers / symbols recommendations that you may be familiar with. It has nominally repudiated all of those guidelines, and the guy wrote them [says he was wrong][nist].
- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
- [^throttling]: If you run a web service, _please_ prevent rapid or repeated login abuse, both per-account and per-IP, plus any other way to identify abusive attempts.
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, but there's also the "Forgot my password" page that only needs a new password. <s>Annoying</s> _Clever_ users will just use that page instead.</p> <p>To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.
- [^random]: Ideally, this is totally random, but it can be random [within interesting bounds][diceware], assuming there isn't a length limit[^length-limit] on your password.
- [^password-manager]: There are plenty of great password managers out there. I'm hesitant to suggest or denigrate any specific ones, but you should do a little research. You want to see if any particular program is untested (i.e. a toy), cutting corners, or actually good.
- [^length-limit]: There is a special InfoSec hell for anyone who designed a password field for no more than 16 characters. NIST says to allow _at least_ 64 characters.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [password-card]: https://www.passwordcard.org/
- [hibp]: https://haveibeenpwned.com/
- [nist]: https://archive.is/4xffa
- Passwords are annoying. Nobody really _enjoys_ passwords, which is why "The End of Passwords" articles keep circulating. I'm looking forward to the day the prediction comes true, but in the meantime passwords are the most common way to do authentication anywhere with a computer.
- I made a chart to classify the important distinctions in making a new password. I'll elaborate on the regions below.
- 
- ## Bad Passwords
- ### Worst
- #### One of the top-used passwords
- Think `abcdef`, `123456`, `iloveyou`, `Pa$$w0rd`, etc. Most of these fall afoul of any website with criteria, but some of them are crafted specifically to get past the "rules."
- #### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And once that combination is public, anyone can do the same.[^hibp]
- ### Bad
- #### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- #### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- #### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ### Not good
- #### Easy to brute force
- Now we're getting to your real question. Like [tarhalda implies][tarhalda], this is the place where attacks typically fall into two modes:
- ##### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- + The first place they're going to try the password is on the system it came from, but they're going to try it anywhere else you might have an account, too.
- ##### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts.[^throttling] That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make you change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations[^nist] to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate a [diceware password][diceware] and offer it as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The only nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- ## Upshot
- ### Don't
- - Don't use anything that can be tied to you.
- - Don't use anything known to be in use by anyone.
- - Don't try to remember all your passwords.
- ### Do
- - Have something to remember the passwords for you.
- - Have something pick completely random passwords[^random] so they are expensive to crack.
- ### Options
- - A password manager from a reputable source[^password-manager]
- - A FIDO key (please have a backup!)
- - A [password card][password-card]
- - A physical notebook
- [^nist]: Between 2003 and 2017, NIST had the 90-day expiration and letters / numbers / symbols recommendations that you may be familiar with. It has nominally repudiated all of those guidelines, and the guy wrote them [says he was wrong][nist].
- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
- [^throttling]: If you run a web service, _please_ prevent rapid or repeated login abuse, both per-account and per-IP, plus any other way to identify abusive attempts.
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, but there's also the "Forgot my password" page that only needs a new password. <s>Annoying</s> _Clever_ users will just use that page instead.</p> <p>To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.
- [^random]: Ideally, this is totally random, but it can be random [within interesting bounds][diceware], assuming there isn't a length limit[^length-limit] on your password.
- [^password-manager]: There are plenty of great password managers out there. I'm hesitant to suggest or denigrate any specific ones, but you should do a little research. You want to see if any particular program is untested (i.e. a toy), cutting corners, or actually good.
- [^length-limit]: There is a special InfoSec hell for anyone who designed a password field for no more than 16 characters. NIST says to allow _at least_ 64 characters.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [password-card]: https://www.passwordcard.org/
- [hibp]: https://haveibeenpwned.com/
- [nist]: https://archive.is/4xffa
#12: Post edited
Passwords are annoying. That's why there are so many "The End of Passwords" articles. I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.With that out of the way, let me rate the worst passwords to use by category:# Bad PasswordsI'm going to elaborate on the regions of the chart below.- ## Worst
- ### One of the top-used passwords
Think `abcdef`, `123456`, `iloveyou`, `Pa$$w0rd`, etc. Most of these fall afoul of any website with criteria, but some of them are concocted specifically to get past the "rules."- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.[^hibp]- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. Like [tarhalda implies][tarhalda], this is the place where attacks typically fall into two modes:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
+ The first place they're going to try the password is on this system, but they're going to try it anywhere else you might have an account, too.- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts.[^throttling] That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations[^nist] to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- You don't want to use anything that can be tied to you.- You don't want to use anything known to be in use by anyone.- You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password[^length-limit]).Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook.### Be safe!- [^nist]: Between 2003 and 2017, NIST had the 90-day expiration and letters / numbers / symbols recommendations that you may be familiar with. It has nominally repudiated all of those guidelines, and the guy wrote them [says he was wrong][nist].
- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
[^throttling]: If you run a web service, _please_ prevent rapid or repeated login abuse, both per-account and per-IP or other ways of identifying abusive attempts.[^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only uses a new password. <s>Annoying</s> _Clever_ users will just use that page instead.</p> <p>To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.[^length-limit]: There is a special InfoSec hell for anyone who designed a password field for no more than 16 characters. NIST says to allow at least 64 characters.- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
[passwordcard]: https://www.passwordcard.org/- [hibp]: https://haveibeenpwned.com/
- [nist]: https://archive.is/4xffa
- Passwords are annoying. Nobody really _enjoys_ passwords, which is why "The End of Passwords" articles keep circulating. I'm looking forward to the day the prediction comes true, but in the meantime passwords are the most common way to do authentication anywhere with a computer.
- I made a chart to classify the important distinctions in making a new password. I'll elaborate on the regions below.
- 
- # Bad Passwords
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `123456`, `iloveyou`, `Pa$$w0rd`, etc. Most of these fall afoul of any website with criteria, but some of them are crafted specifically to get past the "rules."
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And once that combination is public, anyone can do the same.[^hibp]
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. Like [tarhalda implies][tarhalda], this is the place where attacks typically fall into two modes:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- + The first place they're going to try the password is on the system it came from, but they're going to try it anywhere else you might have an account, too.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts.[^throttling] That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make you change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations[^nist] to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate a [diceware password][diceware] and offer it as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The only nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- ## Don't
- - Don't use anything that can be tied to you.
- - Don't use anything known to be in use by anyone.
- - Don't try to remember all your passwords.
- ## Do
- - Have something to remember the passwords for you.
- - Have something pick completely random passwords[^random] so they are expensive to crack.
- ## Options
- - A password manager from a reputable source[^password-manager]
- - A FIDO key (please have a backup!)
- - A [password card][password-card]
- - A physical notebook
- [^nist]: Between 2003 and 2017, NIST had the 90-day expiration and letters / numbers / symbols recommendations that you may be familiar with. It has nominally repudiated all of those guidelines, and the guy wrote them [says he was wrong][nist].
- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
- [^throttling]: If you run a web service, _please_ prevent rapid or repeated login abuse, both per-account and per-IP, plus any other way to identify abusive attempts.
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, but there's also the "Forgot my password" page that only needs a new password. <s>Annoying</s> _Clever_ users will just use that page instead.</p> <p>To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.
- [^random]: Ideally, this is totally random, but it can be random [within interesting bounds][diceware], assuming there isn't a length limit[^length-limit] on your password.
- [^password-manager]: There are plenty of great password managers out there. I'm hesitant to suggest or denigrate any specific ones, but you should do a little research. You want to see if any particular program is untested (i.e. a toy), cutting corners, or actually good.
- [^length-limit]: There is a special InfoSec hell for anyone who designed a password field for no more than 16 characters. NIST says to allow _at least_ 64 characters.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [password-card]: https://www.passwordcard.org/
- [hibp]: https://haveibeenpwned.com/
- [nist]: https://archive.is/4xffa
#11: Post edited
This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
Let's start with a chart and then talk about the regions.- 
- ## Worst
- ### One of the top-used passwords
Think `abcdef`, `Pa$$w0rd`, `letmein`, `iloveyou`, etc. Most of these fall afoul of any website with criteria, but some of them are concocted specifically to get past the "rules."- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.[^hibp]
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math comes in from Lundin, tarhalda, and the XKCD comic.- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations[^nist] to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password[^length-limit]).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook.
- ### Be safe!
- [^nist]: Between 2003 and 2017, NIST had the 90-day expiration and letters / numbers / symbols recommendations that you may be familiar with. It has nominally repudiated all of those guidelines, and the guy wrote them [says he was wrong][nist].
- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
[^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.- [^length-limit]: There is a special InfoSec hell for anyone who designed a password field for no more than 16 characters. NIST says to allow at least 64 characters.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
- [hibp]: https://haveibeenpwned.com/
- [nist]: https://archive.is/4xffa
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- I'm going to elaborate on the regions of the chart below.
- 
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `123456`, `iloveyou`, `Pa$$w0rd`, etc. Most of these fall afoul of any website with criteria, but some of them are concocted specifically to get past the "rules."
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.[^hibp]
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. Like [tarhalda implies][tarhalda], this is the place where attacks typically fall into two modes:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- + The first place they're going to try the password is on this system, but they're going to try it anywhere else you might have an account, too.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts.[^throttling] That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations[^nist] to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password[^length-limit]).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook.
- ### Be safe!
- [^nist]: Between 2003 and 2017, NIST had the 90-day expiration and letters / numbers / symbols recommendations that you may be familiar with. It has nominally repudiated all of those guidelines, and the guy wrote them [says he was wrong][nist].
- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
- [^throttling]: If you run a web service, _please_ prevent rapid or repeated login abuse, both per-account and per-IP or other ways of identifying abusive attempts.
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only uses a new password. <s>Annoying</s> _Clever_ users will just use that page instead.</p> <p>To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.
- [^length-limit]: There is a special InfoSec hell for anyone who designed a password field for no more than 16 characters. NIST says to allow at least 64 characters.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
- [hibp]: https://haveibeenpwned.com/
- [nist]: https://archive.is/4xffa
#10: Post edited
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- Let's start with a chart and then talk about the regions.
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `Pa$$w0rd`, `letmein`, `iloveyou`, etc. Most of these fall afoul of any website with criteria, but some of them are concocted specifically to get past the "rules."
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.[^hibp]
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations[^nist] to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password[^length-limit]).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook.
- ### Be safe!
- [^nist]: Between 2003 and 2017, NIST had the 90-day expiration and letters / numbers / symbols recommendations that you may be familiar with. It has nominally repudiated all of those guidelines, and the guy wrote them [says he was wrong][nist].
- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.
- [^length-limit]: There is a special InfoSec hell for anyone who designed a password field for no more than 16 characters. NIST says to allow at least 64 characters.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
- [hibp]: https://haveibeenpwned.com/
- [nist]: https://archive.is/4xffa
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- Let's start with a chart and then talk about the regions.
- 
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `Pa$$w0rd`, `letmein`, `iloveyou`, etc. Most of these fall afoul of any website with criteria, but some of them are concocted specifically to get past the "rules."
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.[^hibp]
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations[^nist] to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password[^length-limit]).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook.
- ### Be safe!
- [^nist]: Between 2003 and 2017, NIST had the 90-day expiration and letters / numbers / symbols recommendations that you may be familiar with. It has nominally repudiated all of those guidelines, and the guy wrote them [says he was wrong][nist].
- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.
- [^length-limit]: There is a special InfoSec hell for anyone who designed a password field for no more than 16 characters. NIST says to allow at least 64 characters.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
- [hibp]: https://haveibeenpwned.com/
- [nist]: https://archive.is/4xffa
#9: Post edited
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- Let's start with a chart and then talk about the regions.
- 
- ## Worst
- ### One of the top-used passwords
Think `abcdef`, `Pa$$w0rd`, `letmein`, `iloveyou`, etc. Most of these fall afoul of any website with criteria, but some of them are concocted specifically to get pass the "rules."- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.[^hibp]
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations[^nist] to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password[^length-limit]).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook.
- ### Be safe!
- [^nist]: Between 2003 and 2017, NIST had the 90-day expiration and letters / numbers / symbols recommendations that you may be familiar with. It has nominally repudiated all of those guidelines, and the guy wrote them [says he was wrong][nist].
- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.
- [^length-limit]: There is a special InfoSec hell for anyone who designed a password field for no more than 16 characters. NIST says to allow at least 64 characters.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
- [hibp]: https://haveibeenpwned.com/
- [nist]: https://archive.is/4xffa
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- Let's start with a chart and then talk about the regions.
- 
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `Pa$$w0rd`, `letmein`, `iloveyou`, etc. Most of these fall afoul of any website with criteria, but some of them are concocted specifically to get past the "rules."
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.[^hibp]
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations[^nist] to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password[^length-limit]).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook.
- ### Be safe!
- [^nist]: Between 2003 and 2017, NIST had the 90-day expiration and letters / numbers / symbols recommendations that you may be familiar with. It has nominally repudiated all of those guidelines, and the guy wrote them [says he was wrong][nist].
- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.
- [^length-limit]: There is a special InfoSec hell for anyone who designed a password field for no more than 16 characters. NIST says to allow at least 64 characters.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
- [hibp]: https://haveibeenpwned.com/
- [nist]: https://archive.is/4xffa
#8: Post edited
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- ## Worst
- ### One of the top-used passwords
Think `abcdef`, `pa$$w0rd`, `letmein`, etc. Most of these fall afoul of any website with criteria, but some of them are concocted specifically to get pass the "rules."- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.[^hibp]
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations[^nist] to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password[^length-limit]).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook.
Be safe![^nist]: Between 2003 and 2017, NIST had the 90-day expiration and letters / numbers / symbols recommendations that you may be familiar with. It has nominally [repudiated all of those guidelines][nist].- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.
- [^length-limit]: There is a special InfoSec hell for anyone who designed a password field for no more than 16 characters. NIST says to allow at least 64 characters.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
- [hibp]: https://haveibeenpwned.com/
- [nist]: https://archive.is/4xffa
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- Let's start with a chart and then talk about the regions.
- 
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `Pa$$w0rd`, `letmein`, `iloveyou`, etc. Most of these fall afoul of any website with criteria, but some of them are concocted specifically to get pass the "rules."
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.[^hibp]
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations[^nist] to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password[^length-limit]).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook.
- ### Be safe!
- [^nist]: Between 2003 and 2017, NIST had the 90-day expiration and letters / numbers / symbols recommendations that you may be familiar with. It has nominally repudiated all of those guidelines, and the guy wrote them [says he was wrong][nist].
- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.
- [^length-limit]: There is a special InfoSec hell for anyone who designed a password field for no more than 16 characters. NIST says to allow at least 64 characters.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
- [hibp]: https://haveibeenpwned.com/
- [nist]: https://archive.is/4xffa
#7: Post edited
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `pa$$w0rd`, `letmein`, etc. Most of these fall afoul of any website with criteria, but some of them are concocted specifically to get pass the "rules."
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.[^hibp]
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password[^length-limit]).
Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook. Be safe!- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.
[^length-limit]: There is a special InfoSec hell for anyone who designed a password field for no more than 16 characters.- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
[hibp]: https://haveibeenpwned.com/
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `pa$$w0rd`, `letmein`, etc. Most of these fall afoul of any website with criteria, but some of them are concocted specifically to get pass the "rules."
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.[^hibp]
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations[^nist] to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password[^length-limit]).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook.
- Be safe!
- [^nist]: Between 2003 and 2017, NIST had the 90-day expiration and letters / numbers / symbols recommendations that you may be familiar with. It has nominally [repudiated all of those guidelines][nist].
- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.
- [^length-limit]: There is a special InfoSec hell for anyone who designed a password field for no more than 16 characters. NIST says to allow at least 64 characters.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
- [hibp]: https://haveibeenpwned.com/
- [nist]: https://archive.is/4xffa
#6: Post edited
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `pa$$w0rd`, `letmein`, etc. Most of these fall afoul of any website with criteria, but some of them are concocted specifically to get pass the "rules."
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.[^hibp]
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password[^length-limit]).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook. Be safe!
- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.
[^length-limit]: There is a special InfoSec hell for anyone who designed a password field for under 16 characters.- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
- [hibp]: https://haveibeenpwned.com/
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `pa$$w0rd`, `letmein`, etc. Most of these fall afoul of any website with criteria, but some of them are concocted specifically to get pass the "rules."
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.[^hibp]
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password[^length-limit]).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook. Be safe!
- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.
- [^length-limit]: There is a special InfoSec hell for anyone who designed a password field for no more than 16 characters.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
- [hibp]: https://haveibeenpwned.com/
#5: Post edited
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- ## Worst
- ### One of the top-used passwords
Think `abcdef`, `password`, `letmein`, etc. Usually these fall afoul of any website with "strength" criteria.- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
This is a hedge against those services getting hacked in the future. (Or already being hacked, but no one knows yet.) This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password).- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook. Be safe!
[^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys on operations like this.- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
[passwordcard]: https://www.passwordcard.org/
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `pa$$w0rd`, `letmein`, etc. Most of these fall afoul of any website with criteria, but some of them are concocted specifically to get pass the "rules."
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.[^hibp]
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future (or already hacked, but no one knows yet). This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password[^length-limit]).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook. Be safe!
- [^hibp]: There are free services where you can check your email address(es) or register to be notified if any of them is discovered in a password dump. The original one was called [Have I Been Pwned?][hibp], but there are others now, too.
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys' bespoke hardware on operations like this.
- [^length-limit]: There is a special InfoSec hell for anyone who designed a password field for under 16 characters.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
- [hibp]: https://haveibeenpwned.com/
#4: Post edited
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `password`, `letmein`, etc. Usually these fall afoul of any website with "strength" criteria.
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
It's an incredibly common attack to find an email/password combo and just try that _everywhere._ And _anyone_ can do this once that combo is public.- ## Bad
- ### _Any_ leaked password
Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first, since it's going to try them eventually and there's evidence that _real humans_ used these sequences.Some web services refuse to set your password to anything they've found in password dumps.- ### Any password of _yours_
This is a hedge against those services getting hacked in the future. (Or already being hacked, but no one knows yet.) This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, … Don't do that.- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Whatever.- If the Important Stuff™ is _not_ encrypted, you've already lost it.- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math from Lundin, tarhalda, and the XKCD image comes in.- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the worse mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^1]I haven't seen anyone doing this, but I have wondered whether it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as a possibility without following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it.- The only nice thing in this situation is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, one hopes that it's not that critical a website.The attacker wants your creds to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook. Be safe!
[^1]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys on operations like this.- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `password`, `letmein`, etc. Usually these fall afoul of any website with "strength" criteria.
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password pair and just try that _everywhere._ And anyone can try that combination out once it is public.
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first. It's going to try them eventually, and there's evidence that _real humans_ used these sequences.
- Some web services have recently started reacting to this. I've heard of some that refuse to set your password to the 10,000 most common things they've found in password dumps. I look forward to more of this.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future. (Or already being hacked, but no one knows yet.) This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, and so on. Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Credentials accidentally included in public source code. All these have happened.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it. Sorry.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math comes in from Lundin, tarhalda, and the XKCD comic.
- Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the "worst" or "bad" mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^sequential]
- I haven't seen anyone doing this, but I think it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as an alternative to following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it. If someone wants to devise their own password, they can fulfill all the password requirements just like before.
- The _only_ nice thing about a vulnerable web service is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, we desperately hope that it's not that critical a website.
- What the attacker probably wants is your credentials to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook. Be safe!
- [^sequential]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys on operations like this.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
#3: Post edited
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `password`, `letmein`, etc. Usually these fall afoul of any website with "strength" criteria.
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password combo and just try that _everywhere._ And _anyone_ can do this once that combo is public.
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first, since it's going to try them eventually and there's evidence that _real humans_ used these sequences.
- Some web services refuse to set your password to anything they've found in password dumps.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future. (Or already being hacked, but no one knows yet.) This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, … Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Whatever.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math from Lundin, tarhalda, and the XKCD image comes in.
- - Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the worse mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^1]
I haven't seen anyone doing this, but I have wondered whether it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as a possibility without following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" and force you to use that for computer-to-computer credentials.- - The only nice thing in this situation is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, one hopes that it's not that critical a website.
- The attacker wants your creds to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook. Be safe!
- [^1]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys on operations like this.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `password`, `letmein`, etc. Usually these fall afoul of any website with "strength" criteria.
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password combo and just try that _everywhere._ And _anyone_ can do this once that combo is public.
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first, since it's going to try them eventually and there's evidence that _real humans_ used these sequences.
- Some web services refuse to set your password to anything they've found in password dumps.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future. (Or already being hacked, but no one knows yet.) This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, … Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Whatever.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math from Lundin, tarhalda, and the XKCD image comes in.
- - Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the worse mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^1]
- I haven't seen anyone doing this, but I have wondered whether it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as a possibility without following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" for computer-to-computer credentials and force you to use it.
- - The only nice thing in this situation is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, one hopes that it's not that critical a website.
- The attacker wants your creds to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook. Be safe!
- [^1]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys on operations like this.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
#2: Post edited
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's a common way to do authentication.- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `password`, `letmein`, etc. Usually these fall afoul of any website with "strength" criteria.
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password combo and just try that _everywhere._ And _anyone_ can do this once that combo is public.
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first, since it's going to try them eventually and there's evidence that _real humans_ used these sequences.
- Some web services refuse to set your password to anything they've found in password dumps.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future. (Or already being hacked, but no one knows yet.) This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, … Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- If the attacker gets the whole database (not via your password) and the Important Stuff™ is not encrypted, you've already lost it.- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- There is the possibility that a badly designed web service (like the XKCD posits) doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math from Lundin, tarhalda, and XKCD come in.+ The only nice thing is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, one hopes that it's not that critical a website. The attacker wants your creds to try them on GMail, Apple, Amazon, your national Taxation website, your work accounts, etc. If you've avoided password re-use, you're probably safe-ish.- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook. Be safe!
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
- This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
- Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's the most common way to do authentication anywhere with a computer.
- With that out of the way, let me rate the worst passwords to use by category:
- # Bad Passwords
- ## Worst
- ### One of the top-used passwords
- Think `abcdef`, `password`, `letmein`, etc. Usually these fall afoul of any website with "strength" criteria.
- ### A leaked password of _yours_
- Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
- It's an incredibly common attack to find an email/password combo and just try that _everywhere._ And _anyone_ can do this once that combo is public.
- ## Bad
- ### _Any_ leaked password
- Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first, since it's going to try them eventually and there's evidence that _real humans_ used these sequences.
- Some web services refuse to set your password to anything they've found in password dumps.
- ### Any password of _yours_
- This is a hedge against those services getting hacked in the future. (Or already being hacked, but no one knows yet.) This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, … Don't do that.
- ### Stuff about you
- In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
- ## Not good
- ### Easy to brute force
- Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- #### Full database exfiltration
- Sometimes the attacker gets the whole database. This wouldn't be because of _your_ password (unless you're an administrator). It may be a hack of the server. It may be a backup stored improperly. Whatever.
- - If the Important Stuff™ is _not_ encrypted, you've already lost it.
- - If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
- + This is a real thing that real attackers do.
- + Sometimes they sell the hashes to other bad people before they're even cracked.
- + Cracking gets faster all the time, and it's already really fast.
- #### Vulnerable web service
- XKCD posits a badly designed web service that doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math from Lundin, tarhalda, and the XKCD image comes in.
- - Historically, the way that security policies defended against this kind of attack was to expire your password and make _you_ change it. In theory, that still works. You could set a kind-of-hard password that doesn't make any of the worse mistakes and change it every <s>3</s> <s>2</s> <s>1</s> _0.5_ months.
- But that's a terrible user experience. NIST, a US government standards body, changed its longstanding recommendations to suggest longer, easier-to-remember passwords instead of forced expiration. Not to mention: people will just make their password `jimmyjohn-2023Q4` or something and advance it each time. Computers are not great at figuring out the pattern someone used from a single data point.[^1]
- I haven't seen anyone doing this, but I have wondered whether it is reasonable for the service to randomly generate [a diceware password][diceware] and offer that as a possibility without following the "X letters, Y numbers, Z symbols" rules. It's basically the same as how services make a fully random "app password" and force you to use that for computer-to-computer credentials.
- - The only nice thing in this situation is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, one hopes that it's not that critical a website.
- The attacker wants your creds to try them on GMail, Apple, Amazon, your national taxation system, your work accounts, etc. If you've avoided password re-use, you're probably somewhat safe.
- # Upshot
- - You don't want to use anything that can be tied to you.
- - You don't want to use anything known to be in use by anyone.
- - You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password).
- Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook. Be safe!
- [^1]: The server can't look directly at your old passwords to compare with the new one you're setting since they old ones are hashed. You may protest that the "change password" page says "Old password / New password / Retype new password." Yes, that's true. Let me introduce you to the "Forgot my password" page that only takes a new password. <s>Annoying</s> _Clever_ users will just use that page instead.<br/><br/> To catch someone using an unsafe scheme, the server has to speculatively invent all old passwords they _might_ have used for their last password and _hash each of them._ That's designed to be expensive since it's basically an attempt to crack the server's own password database. You can't compete with the bad guys on operations like this.
- [tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
- [diceware]: https://diceware.dmuth.org/
- [passwordcard]: https://www.passwordcard.org/
#1: Initial revision
This started out as a comment on [tarhalda's answer][tarhalda], but it became too long and unwieldy for a comment thread.
Passwords are annoying. That's why there are so many "The End of Passwords" articles. And I'm looking forward to that day, but in the meantime it's a common way to do authentication.
With that out of the way, let me rate the worst passwords to use by category:
# Bad Passwords
## Worst
### One of the top-used passwords
Think `abcdef`, `password`, `letmein`, etc. Usually these fall afoul of any website with "strength" criteria.
### A leaked password of _yours_
Remember that forum you signed up for that was later hacked? You better hope you never used that password with that email address anywhere else.
It's an incredibly common attack to find an email/password combo and just try that _everywhere._ And _anyone_ can do this once that combo is public.
## Bad
### _Any_ leaked password
Consider this to be the next step down of "One of the top-used passwords." Brute-forcing may as well try these first, since it's going to try them eventually and there's evidence that _real humans_ used these sequences.
Some web services refuse to set your password to anything they've found in password dumps.
### Any password of _yours_
This is a hedge against those services getting hacked in the future. (Or already being hacked, but no one knows yet.) This also includes cute password "schemes" like `n79bx4ccb-facebook`, `n79bx4ccb-microsoft`, … Don't do that.
### Stuff about you
In all likelihood, this is already covered by "Any leaked password." But just in case, I'm adding the "movie detective" style passwords where they try your daughter's birthday, your favorite poet, or whatever.
## Not good
### Easy to brute force
Now we're getting to your real question. This (like tarhalda implies) is the place where attacks are really situational:
- If the attacker gets the whole database (not via your password) and the Important Stuff™ is not encrypted, you've already lost it.
- If the Important Stuff™ _is_ encrypted, a good place for the attacker to start would be to crack the password hashes and see if those creds still work on the live system.
+ This is a real thing that real attackers do.
+ Sometimes they sell the hashes to other bad people before they're even cracked.
+ Cracking gets faster all the time, and it's already really fast.
- There is the possibility that a badly designed web service (like the XKCD posits) doesn't throttle password guesses or lock you out after enough bad attempts. That's where the math from Lundin, tarhalda, and XKCD come in.
+ The only nice thing is that the attacker probably doesn't care about your data on _this_ site, whatever site it is. If it doesn't restrict suspicious logins, one hopes that it's not that critical a website. The attacker wants your creds to try them on GMail, Apple, Amazon, your national Taxation website, your work accounts, etc. If you've avoided password re-use, you're probably safe-ish.
# Upshot
- You don't want to use anything that can be tied to you.
- You don't want to use anything known to be in use by anyone.
- You want to have a system for picking passwords that is expensive and hard to crack. Ideally, this is totally random, but it can be random [within interesting bounds][diceware] (assuming there isn't a length limit on your password).
Use something that is genuinely random and does not require you to remember all the passwords. This could be a password manager from a reputable source. It could be a FIDO key (please have a backup). It could be [a password card][passwordcard]. It could be a physical notebook. Be safe!
[tarhalda]: https://software.codidact.com/posts/290488/290489#answer-290489
[diceware]: https://diceware.dmuth.org/
[passwordcard]: https://www.passwordcard.org/


















